ABSTRACT
Many Internet of Things (IoT) services utilize an IoT access network to connect small devices with remote servers. They can share an access network with standard communication technology, such as IEEE 802.11ah. However, an authentication and key management (AKM) mechanism for resource constrained IoT devices using IEEE 802.11ah has not been proposed as yet. We therefore propose a new AKM mechanism for an IoT access network, which is based on IEEE 802.11 key management with the IEEE 802.1X authentication mechanism. The proposed AKM mechanism does not require any pre-configured security information between the access network domain and the IoT service domain.
It considers the resource constraints of IoT devices, allowing IoT devices to delegate the burden of AKM processes to a powerful agent. The agent has sufficient power to support various authentication methods for the access point, and it performs cryptographic functions for the IoT devices. Performance analysis shows that the proposed mechanism greatly reduces computation costs, network costs, and memory usage of the resource-constrained IoT device as compared to the existing IEEE 802.11 Key Management with the IEEE 802.1X authentication mechanism
IEEE 802.11 AUTHENTICATION AND KEY MANAGEMENT MECHANISM
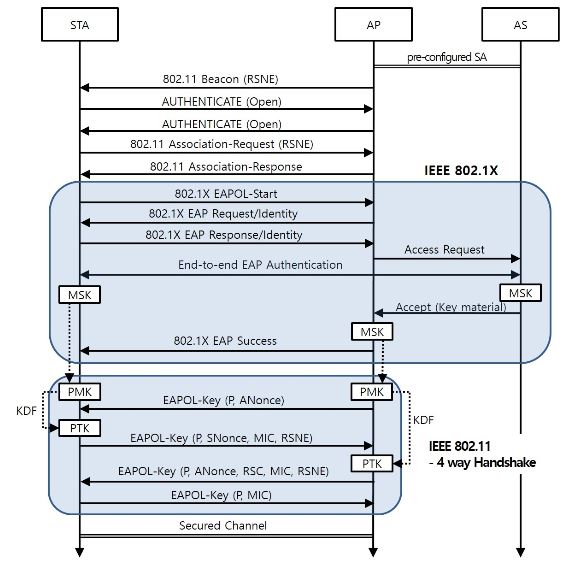
Figure 2. Sequence Diagram of the New Node Attachment in IEEE 802.11 with IEEE 802.1X
Figure 2 presents a sequence diagram for the SA establishment between a station (STA) and the AP to which the STA is associated. Table 1 specifies the notations in the figure. The SA establishment is performed in two phases. Firstly, on behalf of the AP, a STA and the AS authenticate each other and generate a MSK. The AS notifies the AP of the results of the mutual authentication and delivers the MSK to the AP. Then, the session keys are derived from the MSK at the STA and the AP. The four-way handshake is used at this phase.
IOT AUTHENTICATION ARCHITECTURE
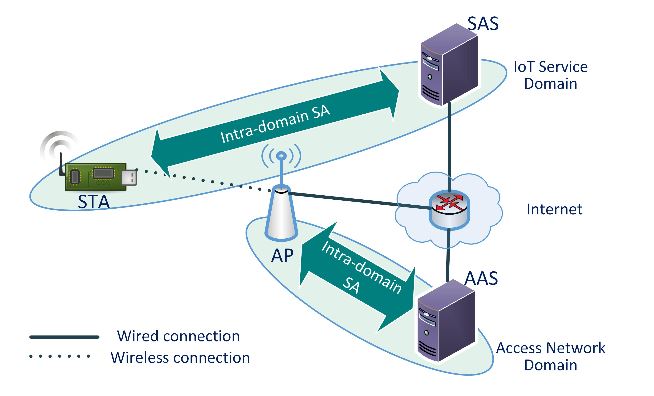
Figure 3. IoT Authentication Architecture
Figure 3 shows the network architecture for the proposed mechanism. The network has two types of domains: the IoT service domain and the access network domain. An IoT service domain consists of STAs and a SAS. The access network domain consists of APs and the AP-side authentication server (AAS). Multiple IoT service domains can share the same access network. Each IoT service domain has a unique domain identifier. The intra-domain SA between the STA and the SAS in the figure indicates that there is a pre-configured Security Association between them. However, in order for them to communicate directly, the STA must access the internet. It is possible after the AKM has been successfully finished and the AP allows the STA to access the network.
PROPOSED AUTHENTICATION AND KEY MANAGEMENT PROCEDURE
This phase follows the open authentication and association procedure defined in the IEEE 802.11-2012 standard. An IoT domain element (IDE) is included in the beacon of an AP if the AP supports the IoT association described in this section. The IDE is a newly defined information element that has an access network identifier of two octets in length. The STA selects an AP that advertises the access network identifier matching an entry in the list of potential access network identifiers with which it can associate.
SECURITY EVALUATION
In this section, we provide details of the security analysis of the proposed AKM mechanism. The first subsection section shows that the proposed scheme provides secure key agreement and mutual authentication. Next, the subsequent subsections introduce attacks that are prevented by the proposed scheme. For the sake of convenience, we designate each of the messages used in the proposed protocol according to a phase alphabet and a message sequence number. For example, D1 represents the first message of phase D.
RELATED WORK
Bonetto et al proposed a security protocol stack for IoT networks, which includes IoT gateways (GWs). A GW is a special IoT device with unconstrained resources and adapts the communication between the other IoT devices and the remote peer via access network infrastructures. They proposed an AKM mechanism to attach an IoT device to an access network (Figure 4). It uses EAP, carried by Protocol for Carrying Authentication for Network Access (PANA) between the IoT device and the GW. The GW and the IoT device derive a PaC-EP Master Key (PEMK), and shares it with the Enforcement Point (EP). Consequently, a PEMK-based secure channel is established between the IoT device and the EP.
PERFORMANCE ANALYSIS OF THE PROPOSED MECHANISM
In this section, we present the performance analysis of the proposed mechanism focusing on the resource consumption of the IoT device. It is compared to the existing IEEE 802.11-2012 with IEEE 802.1X AKM (shortly refer to it as ‘802.11 AKM’ in this section). The 802.11 AKM in this section is assumed to use the Robust Security Network Association (RSNA) default AKM suite, CTR with CBC-MAC Protocol (CCMP) cipher suite, and the EAP with Transport Layer Security protocol (EAP-TLS) with RSA based certification and key exchange.
CONCLUSIONS AND FUTURE WORK
The proposed AKM mechanism establishes an SA between a resource-constrained IoT device and an AP of an accessing network. It minimizes the number of cryptographic processes required on the IoT device by delegating the mutual authentication and the KDF processes of the device to the SAS. Compared to IEEE 802.11 with IEEE 802.1X AKM, the proposed mechanism reduces almost all the computational costs and about 79% of network costs. In addition, cryptographic functions can be replaced with new ones without affecting the resource-constrained devices.
The proposed mechanism also reduces the authentication workload of the AP as the AP authenticates the SAS only once for all STAs belonging to the SAS. This improves the scalability of the AP to a large number of STAs. Other key management protocols, such as re-keying, can be easily applied to the proposed mechanism. For future work, we intend to study hierarchical keying for Extended Service Set (ESS). By using hierarchical keying, the SAS authenticates with an ESS, rather than with an AP, and the APs that belong to the ESS can establish SAs with the STAs that are registered at the SAS, without further authentication.
Source: Korea University
Authors: Ki-wook Kim | Youn-hee Han | Sung-gi Min